Risk register is created at the end of the Identify Risks process and this is the only output of the process. At this stage, the risk register is created only with initial entries. But, as other risk management processes happen we will see an increase in level and type of information and the risk register will get updated accordingly.
The Risk register at this stage contains:
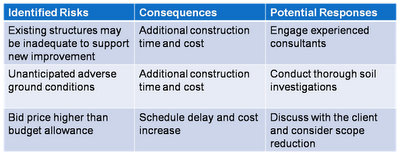
A sample Risk Register is shown below with three identified risks in a construction project. Please take note that in a real project there may be many more risks that have to be identified.
The Risk register at this stage contains:
- List of identified risks: Identified risks are described in as much detail as possible
- List of potential responses: The actual responses for identified risks will only be finalized during the “Plan Risk Responses” process. But, it is good to discuss potential responses while identifying the risks and the contributor to the risk identification would be in a good position to provide some input based on his/ her experience in other projects. This also will be useful as inputs to “Plan Risk Responses” process at a later stage.
- The main aim of the Risk Register at the end of “Identify Risks” process is to identify and record all the risks that can be foreseen. But, as we might have gone through some of the analysis like Cause and Effect Diagram or Root Cause Analysis or Influence Diagram or SWOT Analysis and so on, it would be good if we can include other information like “Root causes” in the risk register
A sample Risk Register is shown below with three identified risks in a construction project. Please take note that in a real project there may be many more risks that have to be identified.